Understanding Red Hat File System Permissions
This is an overview of everything permissions based.
You will learn about
- How to find permissions
- File Permissions
- Umask
- Masking
How to find file and file system permissions
There are a number of different ways to find out file permissions in Linux.
Stat command
One of my favourite Linux commands is the stat command.
Stat – gives you detailed information about the file permissions.
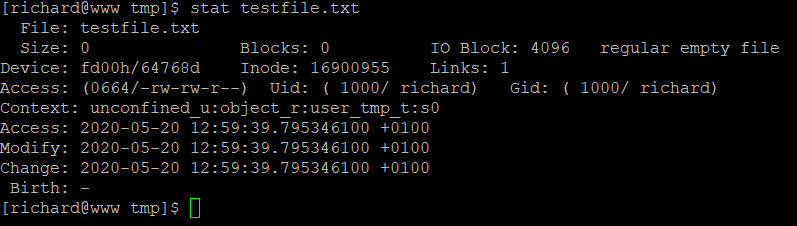
There are a number of operator parameters to refine the stat command
-f, –filesystem
display filesystem status instead of file status
-c, –format=FORMAT
use the specified FORMAT instead of the default
-L, –dereference
follow links
-Z, –context
print the SELinux security context
-t, –terse
print the information in terse form
–version
output version information and exit
The LS command
Every Linux administrator has used this command before. It is used to list the contents of a directory, but it also displays a great number of information about permissions.
ls -l
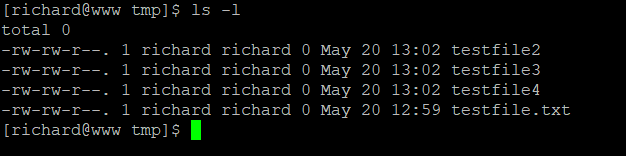
The command gives you the read/write/execute permissions for the Owner / Group / Everyone. The permissions are given in the octal format.
Octal permissions
- 4 = read
- 2 = write
- 1= execute
- (add them up to get the octal value)
StickyBit
A Sticky bit is a permission bit that is set on a file or a directory that lets only the owner of the file/directory or the root user to delete or rename the file.
Sticky bits are very useful on sFTP servers when multiple users have access to a files system. Files can be written to directory by anyone, but only the owner can remove the files.
The sticky bit is represented by a full stop (period) .
drwxrwxrwt. 14 root root 4096 Jan 22 07:24 /tmp
Chmod
chmod is a command to change the permissions of a file. the command and system call which is used to change the access permissions of file system objects. It is also used to change special mode flags. The request is filtered by the umask. The name is an abbreviation of change mode.
chmod 754 myfile
Chown
The Chown command is used to change the owner/group of a file or folder.
Change the owner of a file
chown root testfile1
Change the group of a file
chown :wheel testfile2
Change owner and group of a file
chown rich.bailey:sysadim testfile3
Umask
Default permissions – When a file or directory is created it has to have some set of default permissions. Linux by default assigns Read and Write permissions on the user, group, and other sets, for files, but does not assign any execute permissions. Directories, however, get assigned Read, Write and Execute permissions to all sets by default
Masking – Default permissions are fine, but it would be tedious to change them for every new file created.
Masking directories – Directories are similar – we just add the execute bit into the default. Remember that directories need the execute bit so a user can navigate into the directory. 777 – default
Setting the mask can be done using the umask command. umask is not persistent. It can be set for a specific task in a script, meaning that all new files created during the script will have their permissions masked differently than the default.
Persistent Settings
Two files – /etc/profile and /etc/bashrc control the umask settings for both interactive and login shells. Note that the method they do so contains a conditional statement – so root and other system accounts have a different umask from normal user accounts
RHCSA MiniSeries
Part 1 – How to use Grep and Regular Expressions (RegEx)
Part 2 – How to manipulate files in RedHat
Part 3 – Red Hat Permissions
Part 4 – How to change the root password on Red Hat
Part 5 – How to use Red Hat as a virtual machine host
Part 6 – How to configure local storage
Part 7 – how to manage users and groups in Red Hat Linux
Part 8 – how to configure NTP Network Time Protocol in Red Hat




7 Responses
[…] Part 3 – Red Hat Permissions […]
[…] Part 3 – Red Hat Permissions […]
[…] Part 3 – Red Hat Permissions […]
[…] Part 3 – Red Hat Permissions […]
[…] Part 3 – Red Hat Permissions […]
[…] Part 3 – Red Hat Permissions […]
[…] Part 3 – Red Hat Permissions […]