How to Reset a Lost Root Password in Linux (RHEL, CentOS, Fedora)

Being locked out of a server because of a lost or undocumented root password is a stressful situation for any system administrator. Whether you’ve inherited a machine with no credentials or an OS error has left your system in a read-only state, regaining access is critical.
While you’d normally use the passwd command to change a user password, you can’t log in to do that for root. This guide provides a clear, step-by-step method to recover the root password on modern systemd-based Linux distributions like RHEL, CentOS, and Fedora.
Prerequisites: You must have physical or remote console access to the machine to interact with the bootloader.
The 5-Step Root Password Reset Process
This procedure involves interrupting the server’s boot process, creating a temporary shell, and changing the password before the system fully starts.
Step 1: Interrupt the GRUB2 Boot Menu
First, you need to access the bootloader menu.
- Reboot or Power On the server.
- As the server starts, watch for the GRUB2 boot menu. You may need to press a key to stop the automatic boot countdown. This is often
E,Esc, orShift. - Once the menu appears, use the arrow keys to highlight the default kernel entry and press the
Ekey to edit its boot parameters.
Step 2: Add the rd.break Kernel Parameter
You will now see the boot commands for the selected kernel. Your goal is to tell the system to stop before loading the full operating system.
- Use the arrow keys to find the line that starts with
linux. This line defines how the kernel will boot. - Navigate to the end of that line.
- Add a space, followed by
rd.break. This parameter instructs the system to break the boot process just before control is handed from the initial RAM disk (initramfs) to the main system.- Example line:
linux ... ro root=/dev/mapper/rl-root ... quiet rd.break- Press
Ctrl+XorF10to boot with these modified parameters. The system will boot into an emergency shell prompt.
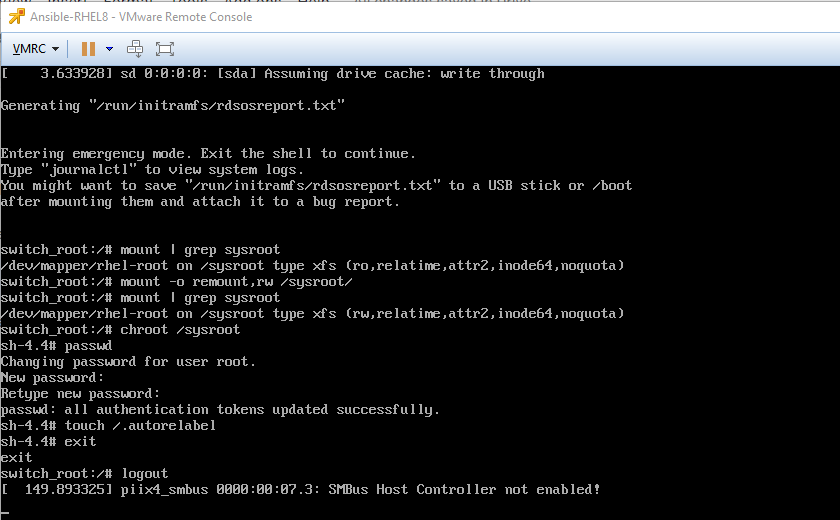
Step 3: Remount the System Root with Write Access
In the rd.break shell, the system’s root filesystem is mounted at /sysroot, but it’s in read-only (ro) mode to prevent accidental damage. You need to remount it with write permissions.
Execute the following command:
mount -o remount,rw /sysrootThis command remounts /sysroot in read-write (rw) mode, allowing you to make changes.
Step 4: Enter the chroot Jail and Change the Password
Now, you need to change the system’s perspective so that /sysroot is treated as the root (/) directory. This is done using the chroot command.
- Access the system’s environment:
chroot /sysroot- You are now in a shell where the commands you run affect the actual system, not the temporary emergency environment. Change the root password using the standard
passwdcommand:
passwd- Follow the prompts to enter and confirm your new, secure root password. You will not see the password as you type.
Step 5: Trigger SELinux Relabel and Reboot
Because you changed a critical file (/etc/shadow) from outside the running OS, you must tell SELinux (Security-Enhanced Linux) to relabel the filesystem on the next boot. This is a mandatory step on systems like RHEL and CentOS.
- Create a special hidden file in the root directory. This file signals the system to perform a full SELinux relabel.
touch /.autorelabel- Note: The
/.autorelabelpath is critical. The leading/ensures it’s created in the root of the chrooted environment. - Exit the
chrootenvironment:Bashexit - Finally, exit the
rd.breakshell to reboot the system:
rebootWhat Happens During Reboot? The SELinux Relabel
After you reboot, do not be alarmed if the boot process takes much longer than usual. You will see messages on the console indicating that SELinux is relabeling files. This process ensures that the security context of the /etc/shadow file (which stores your new password hash) is correct.
If this step is skipped, SELinux policies would prevent you from logging in with the new password, locking you out again. Once the relabeling is complete, the system will reboot a final time, and you can log in with your newly set root password.
Technical Q&A and Best Practices
Q: Why is rd.break used instead of other methods?
A: Linux provides several ways to interrupt the boot process, but rd.break is the most effective for this task on modern systemd systems.
rd.break: Halts the boot process very early, in theinitramfsstage, before the main system’s root filesystem is pivoted to. This gives us a clean environment to remount/sysrootandchrootinto it.rescue.target/emergency.target: These are systemd targets that load much later in the boot process. While they provide a rescue shell, the system is more fully loaded, which can sometimes complicate password resets.
Q: Does this work for other Linux distributions like Debian or Ubuntu?
A: No, this procedure is specific to the RHEL family. Debian and Ubuntu use a different process that typically involves selecting a “Recovery Mode” option from the GRUB menu, which provides a root shell directly without the need for rd.break or manual relabeling.
Q: What are the best practices for root password management?
- Use
sudo: Avoid logging in as root directly. Create an administrative user account and grant it privileges withsudo. This provides better auditing and reduces risk. - Strong Passwords: Always use a complex password for the root account.
- Secure Storage: Store the root password in a secure, encrypted password manager.
- MFA: For critical systems, implement Multi-Factor Authentication (MFA) for an additional layer of security.
Want to learn more about Linux Tech Quickys – click here




Recent Comments